Sophisticated ‘state-sponsored’ spying tool targeted govts, infrastructure for years
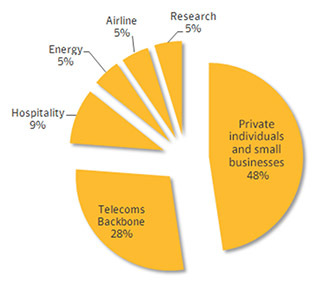
A sophisticated malware dubbed Regin has been used to spy on governments, infrastructure operators and other high-profile targets, security company Symantec has revealed. It also targeted private individuals and businesses, particularly in Russia.
A back door-type Trojan displays a “degree of technical competence rarely seen,” Symantec said in a press release. The complexity of the virus enabled the intruder to create a framework for mass surveillance. Targets include private companies, government entities and research think tanks. Attacks on telecoms companies were allegedly carried out to gain access to calls being routed through their infrastructure.
The company believes that the Trojan was likely developed by a nation state as it took months, if not years to develop such a piece of software and cover up its tracks. Analyzing its further capabilities the company has drawn a conclusion that Regin could be one of the main cyber espionage tools used by the implicated nation state.
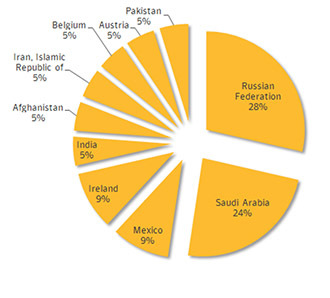
Almost a third of the confirmed infections were discovered in Russia with a further 24 percent in Saudi Arabia. Mexico, Ireland, India, Afghanistan, Iran, Belgium, Austria and Pakistan are also on the list.
“Regin is a highly complex threat which has been used in systematic data collection or intelligence gathering campaigns. The development and operation of this malware would have required a significant investment of time and resources,” Symantec said.
Symantec found that the virus has been used between 2008 and 2011, before being suddenly withdrawn until a new version of the malware resurfaced from 2013 onwards.
Regin uses a modular approach allowing it to load features thatexactly fit the target, enabling a customized spying. “Its design makes it highly suited for persistent, long-term surveillance operations against targets,” the security company says.
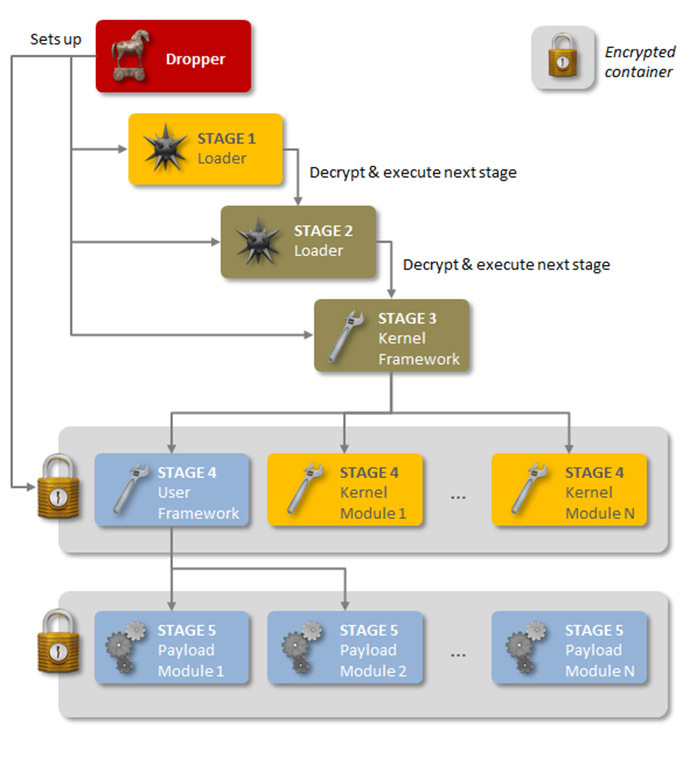
And it’s five-stage loading architecture with special and hidden encryption at each stage makes it similar to Duqu/Stuxnet threats, Symantec said. “Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages. Each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible to analyze and understand the threat,” the press release reads. Furthermore Regin is equipped with a number of stealth features so that even after Trojan’s presence is detected, it is “very difficult to ascertain what it is doing.”
Researchers say many components of the virus remain undiscovered while the threat of additional functionality and versions may still exist.