One bug to rule them all: 'State-supported' Project Sauron malware attacks world's top PCs
Two top electronic security firms have discovered a new powerful malware suite being used to target just dozens of high-value targets around the world. The research shows that it was likely developed on the orders of a government engaging in cyber espionage.
The California-based Symantec has labeled the group behind the attack Strider, while Moscow-based Kaspersky Labs dubbed it ProjectSauron. Both are references to J. R. R. Tolkien’s Lord of the Rings, a nod to the fact that the original malware code contained the word “Sauron.”
READ MORE: 20 Russian high-profile organizations attacked by spy malware in coordinated op – FSB
But behind the playful literary allusions is a powerful piece of software, capable of “harvesting” passwords on entire networks and “modules are designed to perform specific functions like stealing documents, recording keystrokes, and stealing encryption keys from both infected computers and attached USB sticks,” according to Kaspersky.
#ProjectSauron#APT On Par With Equation, Flame, Duqu via @Mike_Mimosohttps://t.co/GrdvCn7CJ7@threatpostpic.twitter.com/aG5OaVZKae
— Kaspersky Lab (@kaspersky) August 8, 2016
The team behind the project has been collecting data illegally since at least October 2011, said Symantec. It had been fooling even the most sophisticated detection systems until last year, when security firms began to identify its components at work, largely due to its choice of targets.
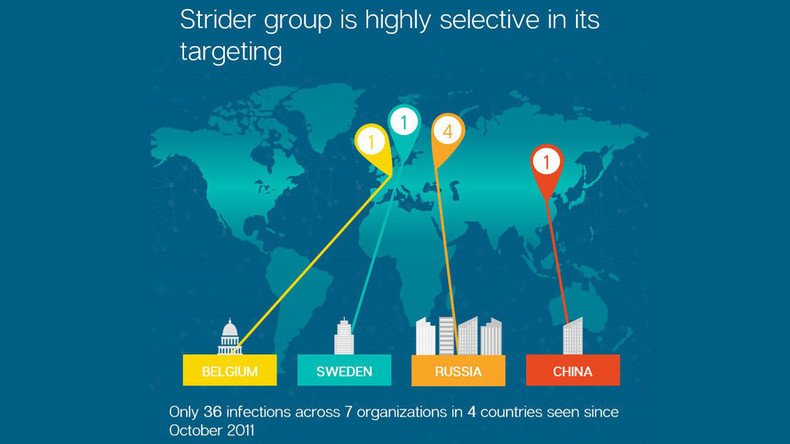
“The group has maintained a low profile until now and its targets have been mainly organizations and individuals that would be of interest to a nation state’s intelligence services,” Symantec wrote. “Strider has been highly selective in its choice of targets and, to date, Symantec has found evidence of infections in 36 computers across seven separate organizations. The group’s targets include a number of organizations and individuals located in Russia, an airline in China, an organization in Sweden, and an embassy in Belgium.”
SWIFT reports new ‘sophisticated’ malware attack https://t.co/zzQc97oRFEpic.twitter.com/noUoBLGnHo
— RT (@RT_com) May 14, 2016
Kaspersky Lab has a different list of infections – which include Rwanda, and unspecified Italian-speaking nations – but says that “government scientific research centers, military, telecommunication providers, finance” were all targets.
#ProjectSauron: top level cyber-espionage platform covertly extracts encrypted govt comms https://t.co/By4TYXwUPLpic.twitter.com/lAdALxFzcT
— Eugene Kaspersky (@e_kaspersky) August 8, 2016
“We think an operation of such complexity, aimed at stealing confidential and secret information, can only be executed with support from a nation state,” said Kaspersky Lab, which says it is cooperating with victims and law enforcement authorities to inform them. “Kaspersky Lab has no exact data on this, but estimates that the development and operation of ProjectSauron is likely to have required several specialist teams and a budget probably running into millions of dollars.”
20 Russian high-profile organizations attacked by spy malware in coordinated op – FSB https://t.co/QoxKG53JuV
— RT (@RT_com) July 30, 2016
Kaspersky Lab compared the threat of the malware to Flame and Duqu, which famously helped another program, Stuxnet, disable Iranian nuclear centrifuges, leading to a shutdown of a uranium enrichment facility in Natanz in 2010.
“Over the last few years, the number of ‘APT-related’ incidents described in the media has grown significantly. For many of these, though, the designation ‘APT,’ indicating an ‘Advanced Persistent Threat,’ is usually an exaggeration,” wrote Kaspersky Lab.
ProjectSauron network sniffer captures files matching these patterns. Interesting Italian keywords: pic.twitter.com/HhDFiMUn9w
— Costin Raiu (@craiu) August 8, 2016
“With some notable exceptions, few of the threat actors usually described in the media are advanced. These exceptions, which in our opinion represent the pinnacle of cyberespionage tools: the truly 'advanced' threat actors out there, are Equation, Regin, Duqu or Careto. Another such an exceptional espionage platform is ‘ProjectSauron’, also known as ‘Strider’.”












