Bad Rabbit cryptoware attack: New virus hits companies in Russia, Turkey, Germany & Ukraine
A new global cyber virus attack began on Tuesday and targeted corporate networks mainly in Russia, cybersecurity company Kaspersky Lab said. A number of companies in Germany, Turkey and Ukraine have been affected on a smaller scale.
“Our observations show that the majority of the attack’s victims are located in Russia. We’re also registering similar attacks in Ukraine, Turkey and Germany, but on a considerably smaller scale. The malware spreads through a number of compromised websites of Russian media outlets,” the company said in its blog.
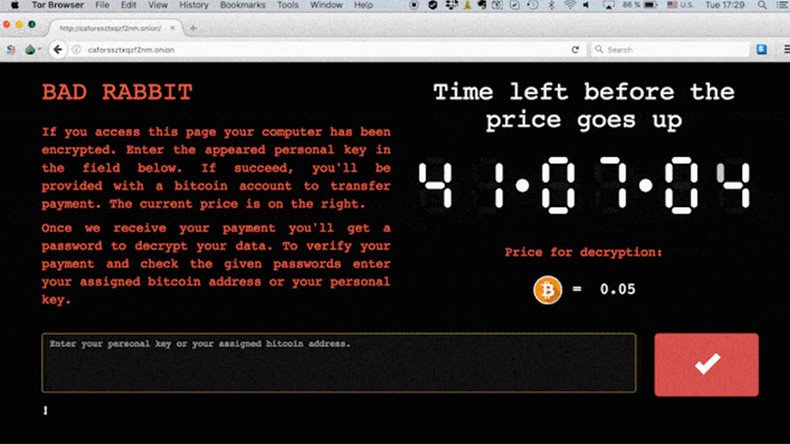
The new virus appears to be dubbed ‘BadRabbit,’ according to a dark net page where the details on ransom for the encrypted files were posted. The initial ransom is 0.05 Bitcoin ($300), but the virus features a timer and promises to raise the price if the ransom is not paid in time.
за разблокировку #BadRabbit требует 0,05 биткоина ($300) pic.twitter.com/i6KXfAexw1
— Group-IB (@GroupIB) 24 октября 2017 г.
The attacks were reported by the Interfax news agency and Fontanka.ru news outlet, as well as by the subway system in the Ukrainian capital, Kiev, and the airport of Odessa. The new cryptoware appears to be deliberately targeting corporate networks, according to Kaspersky Lab.
“Algorithms similar to the ExPetr attack are being used, but we cannot confirm links to ExPetr. We’re still studying the situation,” Kaspersky Lab stated, referring to a major cryptoware attack which hit a number of companies in Russia and Ukraine back in June.
Kaspersky Lab advised those who do not use anti-virus products to restrict execution of certain files (C:\Windows\infpub.dat, C:\Windows\cscc.dat) and shut down the Windows Management Instrumentation (WMI) service.
“In 2017 two major cryptoware epidemics have been registered – we’re talking about the notorious WannaCry and ExPetr (also known as Petya and NotPetya), and now the third one appears to begin,” Kaspersky Lab said.
The WannaCry attack occurred in May and affected up to 300,000 people in more than 150 countries, infecting a number of major companies and institutions, such as the UK’s National Health Service (NHS) and Spanish telecommunications firm Telefonica.
The source of the attack remained undetermined, but earlier this month the head of Microsoft, Brad Smith, pinned the blame for it on North Korea, which allegedly used cyber tools or weapons that were stolen from the National Security Agency in the United States. The top executive, however, did not provide evidence to back his claims.
The Petya family ransomware attack followed WannaCry in June, affecting government and private networks and metro systems in Ukraine. A number of companies were also affected worldwide.
The US government has issued a warning on the BadRabbit attack, urging users not to utilize unsupported and outdated software. According to the US Computer Emergency readiness team (US-CERT), the virus might be a new variant of the Petya family ransomware.
“US-CERT has received multiple reports of Bad Rabbit ransomware infections in many countries around the world,” US-CERT said in a statement, adding, that it “discourages individuals and organizations from paying the ransom, as this does not guarantee that access will be restored.”













