Apple Face ID can be outsmarted using mask, says cybersecurity firm (VIDEO)

A cybersecurity company claims it has already beaten Apple’s Face ID security measure, just one week after the international release of the tech giant’s new iPhone X device.
Vietnamese firm ‘Bkav’ claims it took less than a week and a mere US$150 to outsmart the supposedly sophisticated AI technology, which Apple Senior Vice President Phil Schiller said had been perfected by the company’s engineering team.
READ MORE: New iPhone X owners complain of ‘green line of death’ on screen of $999 device (PHOTOS)
“They have even gone and worked with professional mask makers and makeup artists in Hollywood to protect against these attempts to beat Face ID. These are actual masks used by the engineering team to train the neural network to protect against them in Face ID. It's incredible", said Schiller at Apple’s Keynote in September.

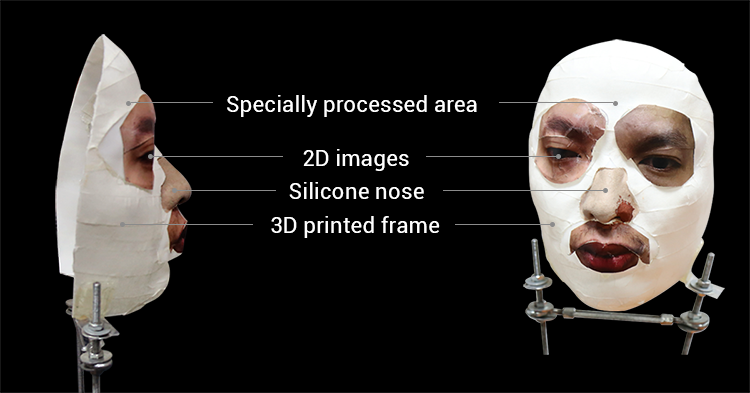
Bkav says the technology was easier to crack than expected, claiming the key to outsmarting the tool is understanding Apple’s AI. The team says they used a 3D-printing machine, and a combination of makeup and 2D images to create the mask.
“You can try it out with your own iPhone X, the phone shall recognize you even when you cover a half of your face. It means the recognition mechanism is not as strict as you think,” said a Bkav representative.
“Apple seems to rely too much on Face ID's AI. We just need a half face to create the mask. It was even simpler than we ourselves had thought.”
READ MORE: Apple finds new offshore haven to stash its cash, avoiding billions in tax
The team’s effort differs from similar attempts to fool the biometric system. Wired.com, for example, spent one month and “thousands of dollars on every material we could imagine to replicate [the subject’s] face, down to every dimple and eyebrow hair,” only to come up short.
Bkav say their goal behind debunking the Face ID phenomenon is to reestablish their theory, which they’ve held since facial recognition was introduced in lieu of a passcode for laptops in 2008, that it is an not an effective security measure.