Google messaging service hacked, sends malware to Android users – Kaspersky

Russia’s Kaspersky Lab has found a backdoor in Google Cloud Messaging service (GCM) used by hackers to steal Android users’ data and force them to send paid messages. The scheme is only stoppable by Google, as it relies on stolen IDs of GCM developers.
The Russian computer security firm on Tuesday said it had
notified Google of a security breach in its service, which
enabled the hackers to register Trojan and Backdoor malware in
the network of the internet giant.
“Such tactics rule out the possibility to block access to
master server directly on the infected phone,” the Kaspersky
team warned in a statement on its website.
Thus, if an Android user is lured into installing some
applications containing the malware, he is doomed to have his
money or private data stolen – unless Google intervenes.
Blocking the accounts of GCM developers, who’s virtual IDs have
been compromised and used for Trojan’s registration, is the only
way to stop the malicious algorithm, Kasperky Lab explained.
The anti-virus developers have been warning that over the past
year cybercriminals have become increasingly active in targeting
tablets and smartphones – especially Android devices – with
malicious software.
The software may often be disguised as an installation package of
a popular mobile application, such as a game or a browser.
Kaspersky Lab expert Roman Unuchek said a typical example of such
a trap for Android users – dubbed Trojan-SMS.AndroidOS.OpFake.a –
has already been detected in 97 countries. The firm has come
across over 1 million different installation packages containing
the malware.
Once installed, this Trojan lets the hackers steal or delete
phone contacts or messages of the Android device owner, send
short messages or ads linking to malware to his friends – and,
ultimately, secretly send “premium” texts to certain numbers, for
which the owner will have to pay a tidy sum.
Another Trojan of the kind, which particularly targets Russia and
the CIS countries, has been discovered by Kaspersky Lab a
staggering 4.8 million times.
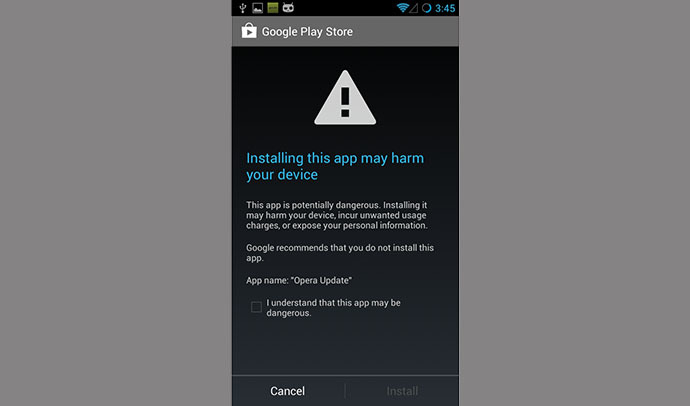
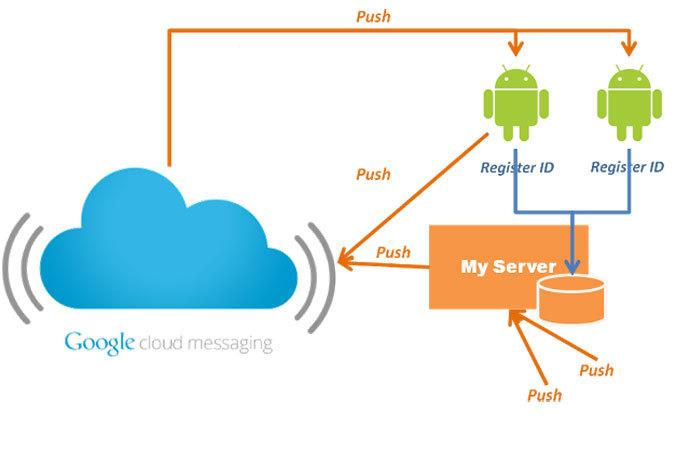
Both programs register within the GCM service, Unuchek notes. In
some cases, Google Play Store – the resource monopolizing the
distribution of all Android apps – may even warn the users of a
potential danger before the installation, but many choose to
ignore the warning message.
According to data published on Kaspersky Lab’s website, up to
12,000 new mobile threats in a form of malware are discovered
monthly by the computer security firm. 99% of all such malware is
said to have targeted the Android platform last year.














