‘Equation Group’ hackers tied to NSA after new Kaspersky Labs report surfaces

Researchers at Kaspersky Labs have not directly stated that the US National Security Agency is tied to a prolific group of hackers that has launched hundreds of attacks in dozens of countries, but a new report has uncovered the clearest link yet.
In a new report, Moscow-based Kaspersky Labs said the kind of operation being run by the hacking collective known as the Equation Group could only be possible with the vast resources of a nation-state behind it. Again, Kaspersky did not specifically cite the NSA in connection to the Equation Group, but the discovery of a new coding artifact strongly links the hackers to the American spy agency.
READ MORE: ‘Equation Group’ hackers attacked 30+ nations with NSA-style tech
As researchers combed through the Equation Group’s main spy platform, dubbed “EquationDrug,” they found the coding artifact "BACKSNARF_AB25." As reported by Ars Technica, the word “BACKSNARF” was also the name of a project linked to the NSA’s Tailored Access Operations, which collects data on computer networks used by foreign countries. The string of letters can be found in this undated NSA document that had previously been leaked online.
The simple presence of the string “BACKSNARF” does not completely prove the Equation Group is connected to the NSA, but Dan Goodwin at Ars Technica said “the chances that there were two unrelated projects with nation-state funding seems infinitesimally small.”
Interestingly, Kaspersky’s research also analyzed timestamps to determine when the hackers were most active. The results showed the group was active during a typical five-day work week, from Monday to Friday, with little to no work being done on the weekends.
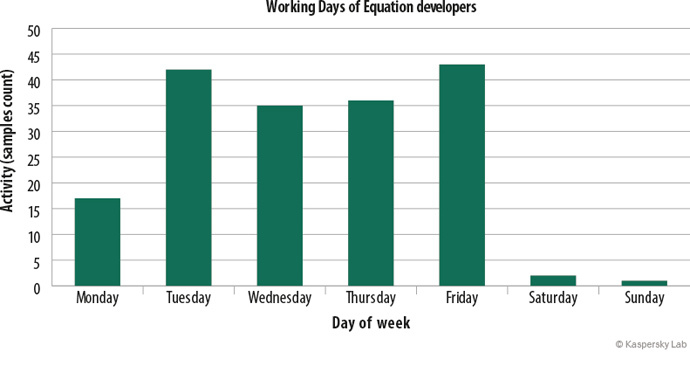
Once they analyzed the hours of the day during which the hackers were most active, they also discovered that they “match the working days and hours of a well-organized software developer from timezone UTC-3 or UTC-4 [observed in the Eastern Time Zone of the US], if you assume that they come to work at 8 or 9 am.”
Notably, the EquationDrug platform was in operation for about 10 years as the hackers operated, though Kaspersky stated in its last report that a new, more advanced cyber-espionage platform, dubbed “GrayFish,” has now taken its place. Since 2001, the group has reportedly launched attacks in more than 30 countries, including Russia, Afghanistan, Pakistan, Syria and dozens more.
The new report also touches on trends Kaspersky has picked up on since it began looking into nation-state hacking capabilities, finding that they are becoming finely honed to impact specific targets.
“It is clear that nation-state attackers are looking for better stability, invisibility, reliability and universality in their cyberespionage tools,” the report reads.
“While traditional cybercriminals mass-distribute emails with malicious attachments or infect websites on a large scale, nation-states create automatic systems infecting only selected users. While traditional cybercriminals typically reuse one malicious file for all victims, nation-states prepare malware unique to each victim and even implement restrictions preventing decryption and execution outside of the target computer.”











