New analysis suggests Guccifer 2.0 files copied locally, not hacked by Russia

Files stolen from the Democratic National Committee (DNC) were likely downloaded to a USB drive by someone with physical access to a computer connected to the DNC network, not hacked remotely by Russia, according to a new analysis.
In an interview with Motherboard in June 2016, the hacker who claimed to be Guccifer 2.0 said he used a zero-day exploit to breach the DNC server and steal files he later published under the title “NGP-VAN.”
The leak was quickly attributed to the Russian government. However, a document published Sunday by an individual known as the Forensicator shows how the 7-zip file published by Guccifer 2.0 was transferred at a speed of 23 MB/s, making it “unlikely that this initial data transfer could have been done remotely over the Internet.”
“The initial copying activity was likely done from a computer system that had direct access to the data,” the report from the Forensicator stated. “By ‘direct access’ we mean that the individual who was collecting the data either had physical access to the computer where the data was stored, or the data was copied over a local high speed network (LAN).”
For his analysis, the Forensicator looked at the data from the 7-zip file which showed the .rar files were built on September 1, 2016, while the other files were last modified on July 5, 2016. When the .rar files are unpacked using a program called WinRAR, their timestamps were preserved from the date they were transferred.
40% of Americans are more cautious about emails after alleged DNC hack – poll https://t.co/VwnfwOVPEF
— RT America (@RT_America) April 6, 2017
The timestamps of those .rar files were relative times, while the times recorded in the 7-zip files are absolute times, recorded in Coordinated Universal Time (UTC). The Forensicator found that if the .rar files were adjusted to Eastern Time, they “fall into the same range as the last modified times for the directories archived in the .rar files.”
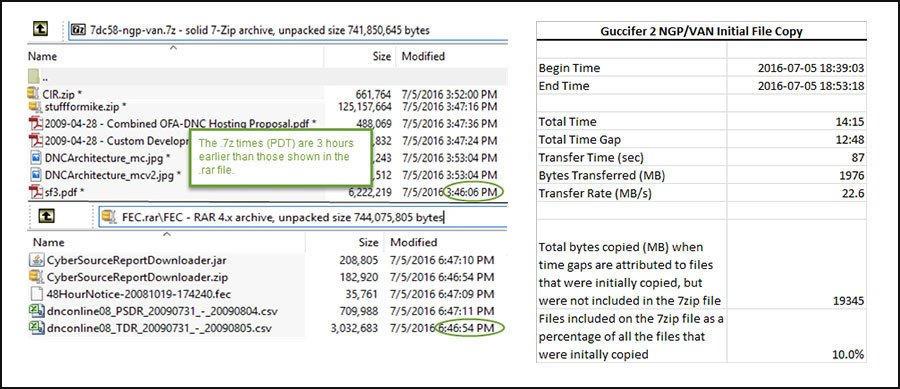
Therefore, the Forensicator concludes that the files were built on a computer system where the Eastern Daylight Savings Time (EDT) timezone setting was in force, meaning that the system was most likely located on the East Coast of the US.
The Forensicator then generated a list of the files sorted by the date they were last modified and imported the list into an Excel spreadsheet. Analyzing the files by date last modified, he observed that the last modified times were clustered together in a 14-minute time period on July 5, 2016.
The analysis of the metadata also found a majority of the time it took for the files to be copies, 12 minutes and 48 seconds of the 14 minutes and 15 seconds, was allocated to “time gaps” that appear between several top-level files and directories. The Forensicator concluded that this indicated that the files were chosen from a much larger collection of files.
Estimating the transfer speed of the files published by Guccifer, the Forensicator concluded that if the 1.98 GB 7-zip archive published by Guccifer was copied at a rate of 22.6 MB/s, and all the time gaps were attributed to additional file copying, the initial file copy would be 10 times larger, or 19.3 GB.














