Homeland In-security? 'Entire generation' of US weapons easily hackable
A report from the US Government Accountability Office paints a grim picture of American military security – or the lack thereof. A host of American weapons can easily be hacked, either due to tech issues or human incompetence.
The GAO report draws on 30 years of Department of Defense data and interviews with dozens of military officials to reveal a broad range of cybersecurity flaws in the world’s most high-tech military apparatus. Security holes were found both in aging systems and systems still under development, suggesting the problem is systemic.
The vulnerabilities are surprisingly low-tech for a country that spends more on the military than the next seven countries combined. Many security flaws involved weak passwords and unencrypted network traffic. Others suggested a poor understanding of network security by military technicians.
DOD likely has an entire generation of systems that were designed and built without adequately considering cybersecurity.
Test teams were able to guess one administrator’s password in nine seconds, while some weapons systems used the default passwords that came with the commercial software that ran the systems. Testers were able to download and delete classified data, take over operators’ screens, and track operators’ activity without alerting them.
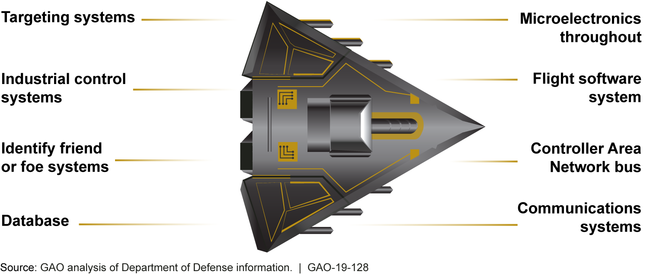
Christina Chaplain, a director at the GAO, told the Intercept the flaws may stem from the military’s overconfidence in its own secrecy measures. Additionally, the Pentagon’s protocols for acquiring weapons systems did not even begin to prioritize cybersecurity until about three years ago, and the agencies responsible for vetting these systems only occasionally overlap with the agencies generally considered knowledgeable about cybersecurity.
Military officials also seemed to have a tenuous grasp of how cybersecurity works. In one case, they opted to ignore repeated breach warnings because they were accustomed to the program malfunctioning. In another case, they left 19 of 20 known vulnerabilities discovered in a previous security audit in place, unable to explain the lapse.
Worse, Chaplain says, the flaws found by the GAO “likely represent a fraction of total vulnerabilities,” since the DOD could not possibly test every connection in the entirety of the sprawling US military computer networks.
The US National Research Council has been warning the Pentagon since 1991 about the possibility of increasing “system disruptions” as weapons systems moved online. The GAO report reveals that the Pentagon essentially ignored that warning, as well as five subsequent warnings just like it.
According to the Defense Science Board, almost every component in the DoD is now networked. Systems connect not only to each other via the Pentagon’s massive set of networks, but may also be linked to external networks, like those of defense contractors, and other systems like electrical grids that in turn connect to the public internet. In short, even the most confidential weapons systems have never been more accessible to the public.
The GAO study comes as the Department of Defense prepares to spend $1.66 trillion on weapons systems development. Despite the gaping security flaws the report illuminates, the watchdog stopped short of making any recommendations.
The US spends hundreds of billions of dollars on its military, but such expenditure is useless if these technologically-advanced systems can be hijacked by its enemies because someone forgot to change the factory-set password.
Like this story? Share it with a friend!














