Court doc shows FBI can access all messages sent over 'anonymous' email service
The United States government seized the contents of every message stored on the servers of a supposedly secure email provider, new documents reveal, and is using that information in other criminal cases.
Kevin Poulsen, a former hacker-turned-tech reporter, wrote for Wired.com on Monday that the US Federal Bureau of Investigation cloned the data being held by a service called Tormail as the result of a separate probe started last year.
The FBI made waves throughout the internet security community back in August when it was discovered that US prosecutors asked police in Ireland to arrest Eric Eoin Marques, a 28-year-old man who administered a hosting provider that offered customers web space on the so-called dark web — a section of the internet that is only accessible through the Tor anonymizer browser and contains an unknown number of hidden portals, including many with content that's illegal under US law.
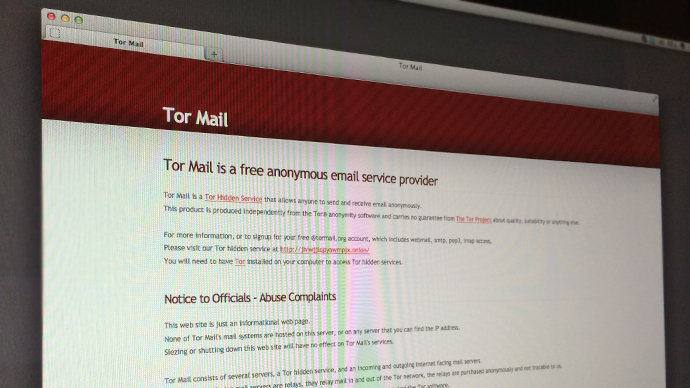
When Marques was arrested last year, US authorities gained control of his company, Freedom Hosting, and the data belonging to customers who had created websites on the dark web. One of those clients was Tormail, a hidden service that boasted of allowing "anyone to send and receive email anonymously" and claimed to never "co-operate with anyone attempting to identify or censor" its users. Only now, though, has it been revealed that the FBI cloned the entirety of that company's info after shutting down its service provider, Freedom Hosting, and customers who relied on it for web space.
“Now the FBI is tapping that vast trove of email in unrelated investigations,” Poulsen wrote early Monday.
Court documents unsealed last week and first spotted by security researcher Brian Krebs revealed that for months the FBI has been interested in an unrelated web operation in which a Florida man allegedly sold counterfeit credit cards and other fraudulent documents to customers over a site called FakePlastic. After law enforcement obtained a search warrant to view the contents of the Gmail account belonging to that man, Sean Roberson, they obtained evidence which suggested he also received and sent messages over a Tormail account — platplus@tormail.net — that quickly became sought by the FBI as well.
“Between July 22, 2013 and August 2, 2013, in connection with an unrelated criminal investigation, the FBI obtained a copy of a computer server located in France via a Mutual Legal Assistance Treaty request to France, which contained data and information from the Tormail email server, including the content of Tormail email accounts,” reads a portion of the criminal complaint against Roberson unsealed last week. “On or about September 24, 2013, law enforcement obtained a search warrant to search the contents of the Platplus Tormail Account, which resided on the seized Tormail server.”
The complaint unearthed by Krebs confirms that investigators involved in the FakePlastic probe did indeed request and receive a second search warrant for the contents of Robeson's Tormail account, but circumvented a likely legal battle over obtaining that information because it was already in the custody of the FBI.
In his own report, Paulsen likened this progression to the contested operations of the US National Security Agency.
“The tactic suggests the FBI is adapting to the age of big-data with an NSA-style collect-everything approach, gathering information into a virtual lock box and leaving it there until it can obtain specific authority to tap it later,” he wrote. “There’s no indication that the FBI searched the trove for incriminating evidence before getting a warrant. But now that it has a copy of TorMail’s servers, the bureau can execute endless search warrants on a mail service that once boasted of being immune to spying,” he added.
Paulsen and others have been quick to liken the Tormail ordeal with the legal issues that for several months have surrounded a similar email provider, Lavabit. That website was shut down last year after its owner, Ladar Levison, was compelled by the federal government to hand over the site's master encryption keys pursuant into an investigation into a single customer. Rather than immediately comply, Levison took his website offline. He and his attorneys are expected to be present in a federal courthouse in Richmond, Virginia on Tuesday when opening arguments begin in their case before the Fourth Circuit Court of Appeals.
Tormail was not affiliated with the Tor Project, a research-education non-profit organization that routinely releases updates to its popular anonymity-enabling web browser.