Newly released NSA slides explain mechanics of US surveillance

In the latest revelations of the NSA leaks scandal, new slides have emerged thoroughly explaining the targeting process of the US government top-secret PRISM program deployed to spy on communication data of targets operating abroad.
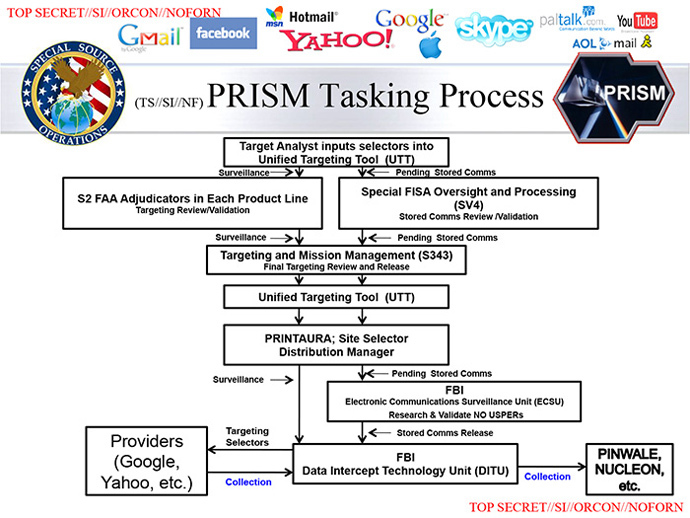
The screenshots published by the Washington Post, detail how
PRISM tasks are issued by analysts and describes the approval
process of an individual requests. To begin with, an NSA analyst
"tasks" PRISM to gather information about a surveillance
target. The system then temporarily freezes that request
and automatically ask for an approval from a supervisor. If
the superior decides that the request possesses a "reasonable
belief" of perceived threat, then PRISM goes to work.
In the surveillance process, NSA often obtains its live data from
the FBI that retrieves matching information, using government
equipment from companies such as Google, Microsoft and Yahoo.
With the participation of those companies, PRISM – and therefore
Washington intelligence workers – "incidentally" have access to
the bulk of Americans’ email, video and voice chat, videos,
photos, voice-over-IP (Skype) chats, file transfers and social
networking details.
For stored data, the FBI deploys its own databases that review
the selects request, before it is forwarded to the NSA.
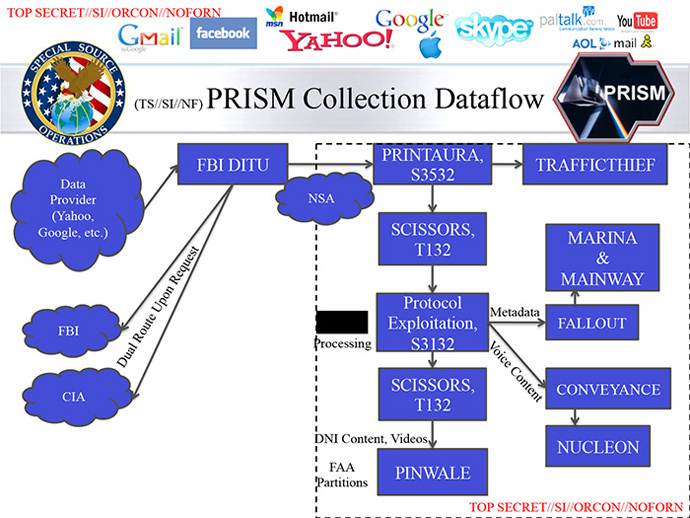
The information is then analyzed and processed by a system that
can interpret voice, text, video and "digital network
information.”
The FBI interceptions from private firms are also being channeled
to more "customers" at the NSA, CIA or FBI. Each target is
then assigned a PRISM case notation which reflects the
availability of real-time surveillance as well as stored data.

Depending on the access to private firm’s information, the NSA
begins to monitor live notifications of the target’s mobile
logs. On the April 5 slide some 117,675 users were targeted in
PRISM database.
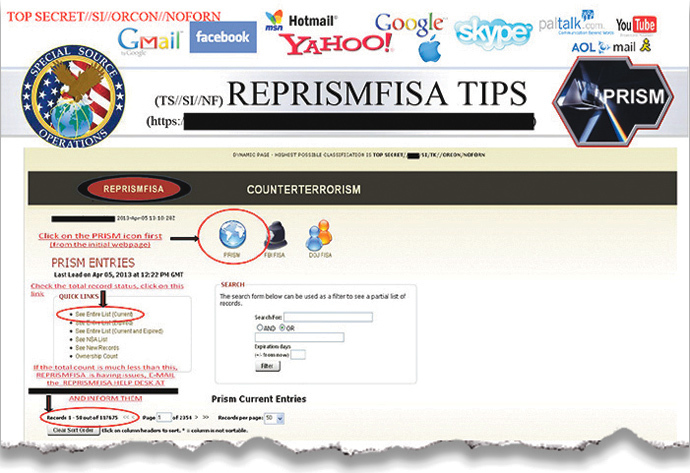
Saturday’s revelations expand the slides that were revealed earlier in June, revealing the existence of the PRISM program, which mines data from the nine leading US Internet companies. Earlier information also revealed the world’s electronic communications flow and Washington’s control over providers.
The NSA venture does not require individual warrants. It is also court approved and is administered through federal judges who rule on the Foreign Intelligence Surveillance Act (FISA).















