Apple’s achilles heel: CIA hacks MacBook computers with ‘Sonic Screwdriver’

WikiLeaks’ latest release of classified CIA documents has revealed the agency’s ability to bypass password protected Apple Macs while the laptop is booting up using a tool called “Sonic Screwdriver.” Monitoring and tracking tools can then be installed.
The CIA’s user guide for Screwdriver, released as part of WikiLeaks’ ‘Dark Matter’ drop, describes the tool as “a mechanism for executing code on peripheral devices while a Mac laptop or desktop is starting up.” Ordinarily, an Apple Firmware password would prevent any changes being made during the startup phase.
However, Screwdriver allows the CIA to infect the very core of the computer making it a stealthy tool undetectable by antivirus software.
READ MORE: #Vault7: WikiLeaks releases ‘Dark Matter’ batch of CIA hacking tactics for Apple products
The malicious code, implanted by the Screwdriver, attacks the computer's Extensible Firmware Interface (EFI), the firmware that loads the computer's operating system (OS). EFI resides outside of the hard disk space on the machine, making it much harder to detect.
The implant code is stored on the firmware of an Apple Thunderbolt-to-Ethernet adapter, a small compact device used for transmitting data (similar to a USB cable), and when it’s plugged into the Thunderbolt port on Macs, it infects them.
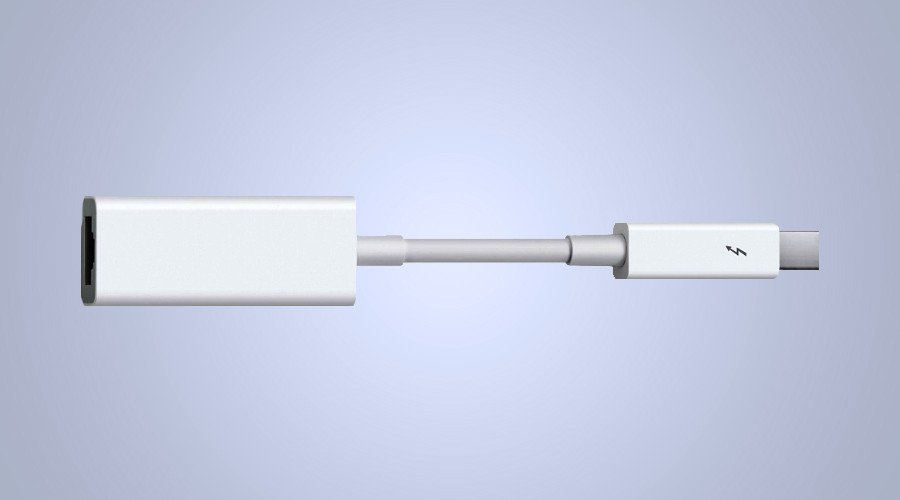
Once inserted into “any Mac laptop or desktop with a Thunderbolt port," the implant code then scans all internal and external hard drives looking for a volume with a specific name - FILER. If this is found, the code will execute, allowing the CIA to take control of the computer, potentially monitoring and transmitting everything that occurs on the machine.
These tools must be physically implanted onto targeted machines. The agency outlines the steps taken by the installer, who must have physical access to the target computer for a period of “1-2 mins” in order to infect it.
CIA monitors phone activity, incl browser history, YouTube video cache & mail metadata - WikiLeaks https://t.co/fnmmPjdsZxpic.twitter.com/dosyNrgNRr
— RT (@RT_com) March 23, 2017
This means that any potential victims would have to leave their machine unattended, although for a brief period, to allow an agent to infect it.
The CIA could, however, intercept the machine, for example, as it was being shipped to a customer from a warehouse, or if a potential target is detained by police and they gave the agency access to it.
Once infected by the Sonic Screwdriver, the firmware implant known as “Der Starke” acts as a loader for the malware “Triton,”details of which were included in Thursday’s release.
READ MORE: #Vault7: Assange says WikiLeaks ‘Dark Matter’ leak ‘small example’ of what’s in store
Triton is the ghost in the machine, which silently monitors its OS activity, potentially sending information back to the agency.
Once installed, the malware can take control of the computer and cannot be removed, even if the OS is uninstalled and reinstalled. It has been compared to a another bug, Thunderstrike, discovered on Macs in 2015.












