Trojan virus secretly uses Tor network to hide bitcoin extortionist

An unusual ransomware Trojan, discovered by cybersecurity experts last month, is the first of its kind to secretly use a Tor anonymizing network to hide its communication with a command-and-control server.
Ransomware is a malicious program that takes control of some functions of a computer and demands payment in exchange for giving it back. Some of them claim to be software used by law enforcement investigating the victim for possession of child pornography or pirated content and require a 'fine' to be paid. Others don't bother with such niceties and simply demand ransom.
Often ransomware searches the computer for files valuable to the user like databases, photos or documents and encrypts them, so that they can no longer be read. Last year CryptoLocker ransomware trojan made waves across the world, netting its criminal operators millions of dollars in bitcoin ransoms before its command-and-control servers were busted in May 2014 by the FBI. In June, a new sample of such encryption malware called Critroni was discovered, and some cybersecurity experts call it a new generation of ransomware.
Critroni is not a variant of previously known ransomware but rather a new development, which uses some techniques never before encountered in such computer viruses, reported the cybersecurity firm Kaspersky Lab, which analyzed Critroni's code.
“This encryption malware is the latest generation of trojan ransomware. The authors used some techniques tested by numerous previous viruses, like the demand to pay ransom in binconis, but also some solution absolutely new for this class of malware,” said Fyodor Sinitsin, chief analyst at the lab.
“This is one of the most dangerous current cyber threats and one of the most sophisticated ransomware programs known today.”
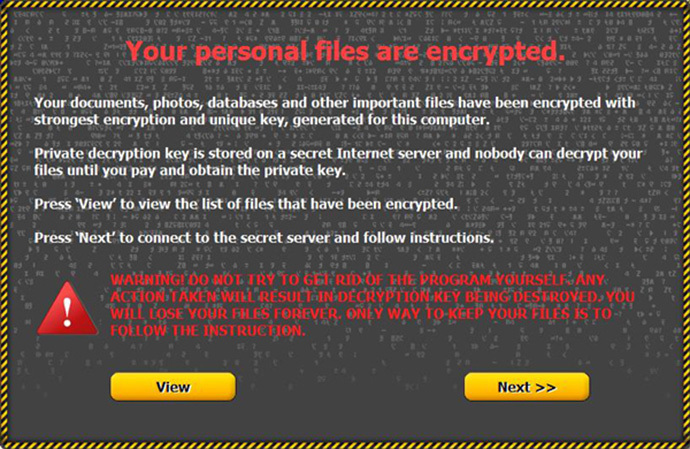
The most unusual feature of Critroni (also dubbed Onion by Kaspersky Lab and named CTB-Locker or Curve-Tor-Bitcoin Locker by its author) is its use of a Tor anonymizing network to communicate with its command server. The malware has to send an encryption key to the criminal and receive the ransom figure for the extortion scheme to work.
Other kinds of malware are known to utilize the protection offered by Tor to hide the attacker, but Critroni is the first ransomware to do it. And it’s the first malware to have Tor code embedded into its own files rather than using the legitimate Tor software to establish the communication.
The ransomware also has a unique encryption scheme to lock the user's files. It first compresses them and then uses an encryption algorithm called ECDH (Elliptic Curve Diffie-Hellman). Unlike the combination of AES and RSA algorithms most popular among ransomware authors, ECDH would not allow the encrypted data to be rescued, even if the virus communication with its command-and-control server is intercepted.
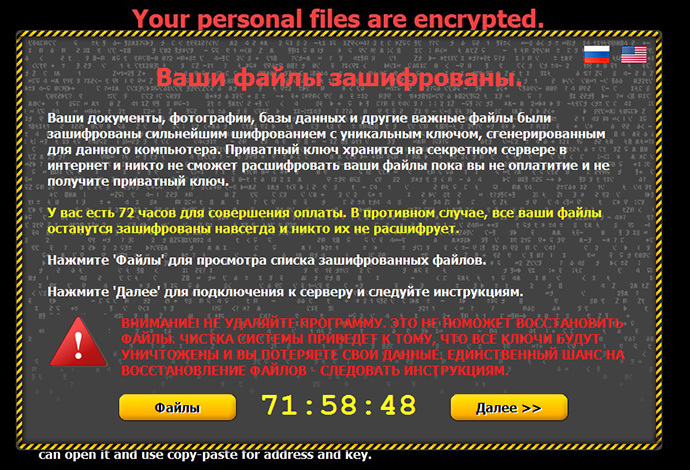
The initial versions of Critroni only had an English language interface, but some of the latest updates added not only a threatening countdown clock that tracks how much time is left to pay up before the 72 hour deadline is reached, but also a Russian-language version of the ransom demand. The majority of infection reports also came from Russia and Ukraine. These facts make Kaspersy Labs believe that the authors of the trojan must be from the former Soviet Union.