Blackhole malware kingpin ‘Paunch’ arrested in Russia
Russian authorities have detained a shadowy cybercriminal known only as “Paunch,” who is responsible for unleashing Blackhole, one of the most dangerous and pervasive malware suites in the history of the Internet.
Reports of the arrest of Paunch were confirmed by the Russian
police to local media and Europol, but officials have so far
refused to disclose the real name of the criminal, whose
activities have likely earned him millions of dollars.
Created in 2010, Blackhole Exploit Kit infects ordinary users’
computers through one of two main techniques: either by making
sure that every time someone enters a particular legitimate
website, which covertly downloads malware onto the web surfer’s
hard drive, or by making a user click on a spam letter that
contains a link to a fake website that does the same thing.
Once the malware is on the computer, it can harm the user in
myriad ways, depending on what sub-programs are installed. Most
common malware extensions try to steal the user’s financial data
from their hard drive, log in all their keystrokes to identify
their passwords, or trick them into paying for anti-virus
software to clear up a non-existent virus.
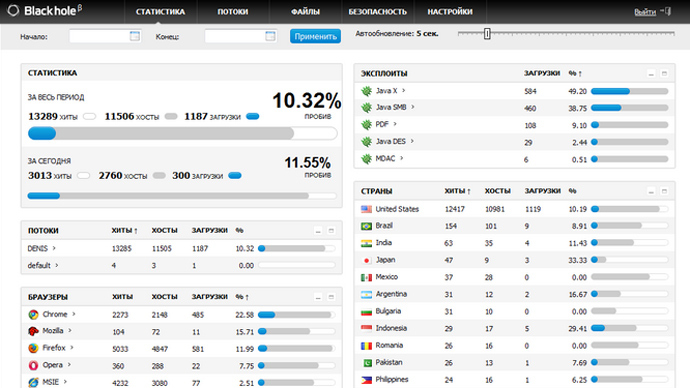
Blackhole was updated as often as twice a day to stay one step
ahead of anti-malware software, though security experts say that
no new versions have appeared this week, another indication that
Paunch is now behind bars.
The success of Blackhole was predicated not only on its
functional versatility and an ability to avoid detection by
anti-virus software, but also on an innovative business model.
Paunch did not appear to use Blackhole to commit cybercrime
himself. Instead he created a price plan, according to which
Internet criminals could rent the suite, which would be hosted on
Paunch’s servers, and use it for their own purposes. Listed
prices varied from $70 per day, to a subscription of $1,500 a
year.
"Both Blackhole and its successor Cool have been very
popular,” Mikko Hypponen, chief research officer at
anti-virus firm F-Secure, told the BBC.
"Users didn't have to be very technical to operate them –
there was a manual that came with them – they just had to get
them running."
Though estimates of Blackhole’s prevalence are fluid, and vary
between different anti-virus companies, it was undoubtedly a
dominant player in the malware market starting from late 2011. At
one point last year, 91 percent of all new computer infections
were transmitted through the suite, according to anti-virus
makers AVG, and Blackhole was responsible for nearly half the
infections for 2012.
But in the copyright-averse world of illegal software, the
success of Blackhole spawned a whole raft of copycats that
toppled Blackhole and its less well-known successor Cool from
their prime positions. Last year, Russian magazine Hacker
reported that to keep up, Paunch was offering $100,000 for fresh
security flaw exploits in popular software that would allow the
program to infiltrate computers in new ways.
AVG reports on its website that Blackhole is currently only the
28th most popular malware transmitter, responsible for about 1
percent of new viruses, with Cool not even in the top 1,000
threats.
“It’s worth remembering that nature abhors a vacuum, and there
would surely be other online criminals waiting to take their
place, promoting their alternative exploit kits and malicious
code,” prominent security expert Graham Cluley wrote on his
blog.
But even if Blackhole in its current form appears to be on its
way out, the arrest of a prominent malware maker, particularly in
Russia, where pursuit of online criminals has historically been
lackadaisical, still represents a breakthrough for the
authorities, especially if his associates have been caught in the
dragnet. Industry experts agree that more than two-thirds of all
malware is currently produced in Russia.
“It’s a very big deal – a real coup for the cybercrime-fighting
authorities, and can hopefully cause disruption to the
development of one of the most notorious exploit kits the web has
ever seen,” wrote Cluley.