‘Elite’ hacking operation ‘The Mask’ targeted govts, diplomats for 7 years

Researchers recently detected a highly sophisticated cyber spying operation, active since 2007, that targeted governments, diplomats, and embassies before it was razed last month.
Kaspersky Labs in Russia identified the attack as “The Mask,” and guessed that the operation most likely comes from a Spanish-speaking nation state, based on its advanced characteristics and Spanish language snippets in its malware. It targeted oil and gas companies in addition to research organizations and activists, Wired reported.
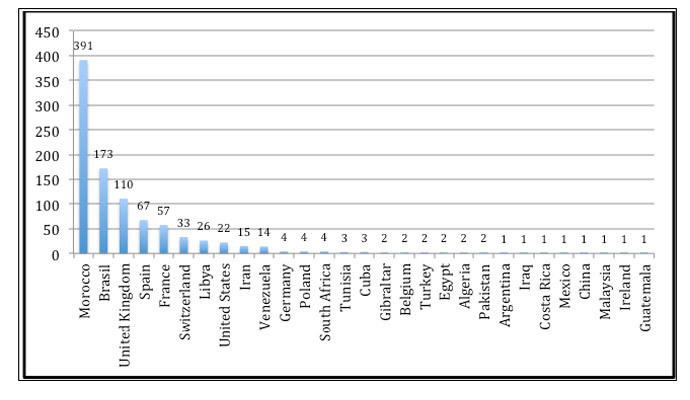
Using complex malware, rootkit methods, and a bootkit to shield continued activity on infected targets, The Mask pursued at least 380 victims in over two dozen countries. It sought documents, encryption keys, data about VPN set-ups, and Adobe signing keys that would offer operators the ability to sign a PDF document as if they owned the key. Most of the targets were in Morocco and Brazil, Kaspersky found.
“They are absolutely an elite APT [Advanced Persistent Threat] group; they are one of the best that I have seen,” Costin Raiu, director of Kaspersky’s Global Research and Analysis Team, said Monday. “Previously in my opinion the best APT group was the one behind Flame...these guys are better.”
APT attacks are associated with high-powered nation-state operations, such as the aforementioned Flame and Stuxnet, created by the US and Israel to damage Iranian nuclear centrifuges. Yet Kaspersky said there were no signs that The Mask – named after Careto, one of the three backdoors used, which means ‘mask’ in Spanish – was developed by the same group. Raiu said this was the first APT malware Kaspersky had seen that came with Spanish language script rather than the usual Chinese.
French company Vupen, which sells exclusive zero-day exploits to law enforcement and intelligence agencies, denied that they supplied attackers with The Mask. Zero-day exploits are, as defined by the Electronic Frontier Foundation, “hacking techniques that take advantage of software vulnerabilities that haven’t been disclosed to the developer or the public.”
In addition, Vupen was suspected based on an exploit it created that targeted the Adobe Flash Player, which was subsequently patched by Adobe in 2012. Kaspersky’s Raiu said they don’t know for certain that a Vupen exploit was used by Mask operators, but he said the code was “really, really sophisticated” and that it’s unlikely they would have developed their own exploit.
Yet Vupen co-founder Chaouki Bekrar denied any involvement, tweeting Monday: “Our official statement about #Mask: the exploit is not ours, probably it was found by diffing the patch released by Adobe after #Pwn2Own.”
Kaspersky first discovered The Mask last year when some of its customers were subjected to an attack that sought to exploit a vulnerability, patched long ago, within some of the company’s security software from a previous generation.
Kaspersky said there were two designs for The Mask’s malware – for Windows and Linux – though they said evidence shows there may also be mobile versions for Android and iPhones/iPads.
Attacks used spear-phishing email campaigns that offered links to webpages that would attach malware onto a machine. Some of the malicious URLs were designed to seem like common-viewed, major news sites in Spain, or the Guardian and The Washington Post, for example.













