MiniDuke: New cyber-attack 'hacks governments' for political secrets

The governments of at least 20 countries may have fallen victim to a sophisticated new cyber-attack. Security experts believe the hackers are attempting to steal political intelligence.
The governments of at least 20 countries may have fallen victim to a sophisticated new cyber-attack. Security experts believe the hackers are attempting to steal political intelligence.
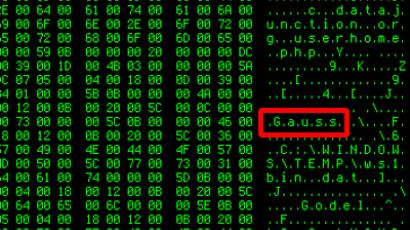
Computer security firms Kaspersky Lab and CrySyS Lab discovered that the malware, dubbed "MiniDuke," targeted government computers in the Czech Republic, Ireland, Portugal and Romania along with think tanks, research institutes and healthcare providers in the United States.
“The technical indicators from our analysis show this is a new type of threat actor that hasn't been seen before,” Kurt Baumgartner, a senior security researcher with Kaspersky Lab, told RT.
Although experts avoid speculating on who the attackers may be, Baumgartner clarified that “based on the target victims and the functionality of the malware” the objective of MiniDuke’s authors is “to collect geopolitical intelligence.”
The threat operates on low-level code to stay hidden, and uses Twitter and Google to get instructions and updates. It allegedly infected PCs when ‘victims’ opened a cleverly disguised Adobe PDF attachment to an email.
“The high level of encryption in the malware and the flexible system it used to communicate with the C2 via Twitter and Google indicates this was a strategically planned operation,” Baumgartner said.
The PDF documents were specifically tailored to their targets, according to the researchers. The attachments referred to highly relevant topics subjects like “foreign policy,” a “human rights seminar,” or “NATO membership plans."
When the files were opened, MiniDuke would install itself on the
user's computer.
So far it is only known that the malware then connects to two
servers, one in Panama and one in Turkey, but security researchers
say there are no clear indications of who was behind the online
attacks.
According to Karpersky Lab the spyware was written in “assembler language,” a low-level code where each statement corresponds to a specific command, and is very small in size, only 20 kilobytes. Assembler language codes are written specifically for each system they are meant to attack, as opposed to higher-level codes, which can infect multiple types of technologies.
The way the malware was created and used indicates that the attackers “have knowledge from the elite, ‘old school’ type of malicious programmers who were extremely effective at creating highly complex viruses in the past,” Baumgartner says. “MiniDuke’s attackers have combined these skills with the newly advanced sandbox-evading exploits to target high-profile victims, which is unique and something we haven’t seen before.”
MiniDuke is a three-stage attack, technology news and
information website, Arstechnica, explains. First it tricks a
victim into opening an authentic-looking PDF document, and then
infected machines start using Twitter or Google “to retrieve
encrypted instructions showing them where to report for additional
backdoors.”
"These accounts were created by MiniDuke’s Command and
Control (C2) operators and the tweets maintain specific tags
labeling encrypted URLs for the backdoors,” Kaspersky Lab said
in a statement. “Based on the analysis, it appears that the
MiniDuke’s creators provide a dynamic backup system that also can
fly under the radar - if Twitter isn’t working or the accounts are
down, the malware can use Google Search to find the encrypted
strings to the next C2.”
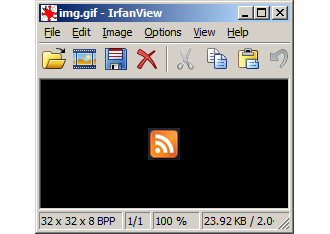
Stages two and three are hidden inside a GIF image file which is downloaded from the command server and “disguised as pictures that appear on a victim’s machine.”
Eugene Kaspersky, founder and chief executive of Kaspersky Lab,
compared the highly-advanced MiniDuke to “malicious programming
from the end of the 1990s and the beginning of the 2000s”,
saying it has the potential to be "extremely dangerous"
because it was an "elite, old-school" attack.
"This is a very unusual cyber-attack," the statement
emailed to RT read.
"I remember this style of malicious programming from the end of the 1990s and the beginning of the 2000s. I wonder if these types of malware writers, who have been in hibernation for more than a decade, have suddenly awoken and joined the sophisticated group of threat actors active in the cyber world. These elite, “old school” malware writers were extremely effective in the past at creating highly complex viruses," Kaspersky's CEO added.
Neither Kaspersky nor CrySyS is disclosing what the malware does
once it takes hold of a victim until they have had a chance to
privately warn infected organizations, Arstechnica
reported.
According to the technology news and information website, at least 60 victims have been affected. Kaspersky has identified at least 23 affected countries, including the US, Hungary, Ukraine, Belgium, Portugal, Romania, the Czech Republic, Brazil, Germany, Israel, Japan, Russia, Spain, the UK, and Ireland.
Revelations about the new malware come two weeks after Silicon
Valley security firm FireEye discovered security flaws in Reader
and Acrobat software.