Brazilian hacker creates Twitter-like app shielded from NSA gaze
In a post-Snowden world where NSA surveillance has been exposed as ubiquitous, one man decided to invent a networking system akin to Twitter, but with one key difference: It would be surveillance-proof and completely decentralized. Meet ‘Twister.’
Miguel Freitas was always a big Twitter fan – especially as it drummed out information on the June mass protests in his native Brazil at a time when no competent up-to-the-minute source existed locally.
But even though Twitter to him symbolized what decentralized media is, Freitas, in an interview with Wired magazine, opened up about his feelings that a world in which the NSA apparently has its nose in every conceivable internet communication would soon need new avenues for information exchange. Ten years of people blissfully communicating their daily routines and locations to Facebook, Twitter and other services have led to large segments of society seeking a newer, upgraded kind of networking, Freitas says.
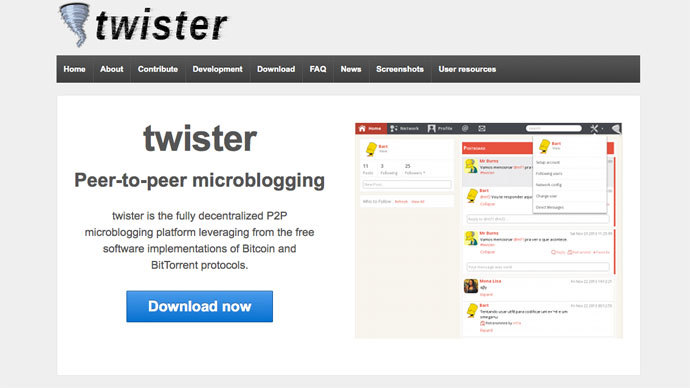
Using his programming skills, Freitas created an open-source Twitter-like service run on a Bitcoin platform. Doing so is key to the technology; Twister allows its users to share posts without them being later stored in one place or server. Its decentralized nature means that it cannot be targeted and erased by a third party. Nor will that party be able to tell if a user is online, what their IP address is and who they follow.
The test version Freitas produced with collaborator Lucas Leal runs on Android, Apple OSX and Linux, and works off a user-run server, or one run by someone the user trusts. Unlike Twitter, Twister’s peer-to-peer architecture works without a central server.
“Twister is a microblogging peer-to-peer platform, that is, it is a distributed system like bittorrent or similar file sharing technologies. Being completely decentralized means that no one is able to shut it down, as there is no single point to attack. The system is also designed so it cannot be censored, freedom of speech cannot be taken from you. And because the cryptography is employed end-to-end, no entity is able to spy on your communications,” Freitas explains on Twister’s homepage.
Using bitcoin’s architecture and verification methods, the app similarly ensures that users do not cheat the system by registering twice or using someone else’s account to post updates. And this system of control is not operated by humans, but by a network of Twister computers run through a BitTorrent protocol (BitTorrent is a peer-to-peer download client), which ensures that posts are automatically and quickly posted, and without a central server.
The Twister protocol works in a similar way to bitcoin miners. But unlike the miners, which unlock digital currency, the miners on Twister are used to verify users. In exchange for allowing themselves to be registered on the network, users receive the ability to share promoted posts. This is something that can be used for both personal and other reasons, even social causes.
There is only one catch, which Freitas points out. Allowing for the possibility that your internet traffic is monitored, that means so is your IP address. And that in turn can be tied to your Twister account. This is why, according to Wired, Freitas suggests that users use the Tor Project’s anonymity software.
In recent months, as more and more Snowden leaks were revealed and the extent of the National Security Agency’s PRISM and other programs was uncovered, the size of Tor’s user base went through the roof.
However, it appears that the NSA also does not wish to let up, as in recent months it has announced plans to create a quantum computer – a machine that handles so many operations per second it can crack virtually any form of online protection.
That does not have to mean the other side will not adapt, of course. The success of Twister is in its completely open-source architecture, which means it can be re-modeled for a variety of uses.














