Snowden leak: NSA plans to infect ‘millions’ of computers

Yet more previously secret surveillance operations waged by the United States National Security Agency were made public Wednesday morning thanks to leaked documents supplied by former NSA contractor Edward Snowden.
The files — published first by The Intercept this week and dissected over the course of a 3,000-word article attributed to journalists Glenn Greenwald and Ryan Gallagher — bring to light a number of previously unreported programs undertaken by the secretive US spy agency, including operations that have given the NSA the potential to infect millions of computers around the world by relying on malicious software that’s sent to targets through surreptitious means.
In recent years, however, the NSA has reportedly made adjustments to these operations that enable them to by carried out automatically without the direct aid of human spies — a decision that experts say is undermining the internet as it is known today,
“Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process,” the journalists wrote.
That automated system named "TURBINE," they said later, is designed to “allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually.”
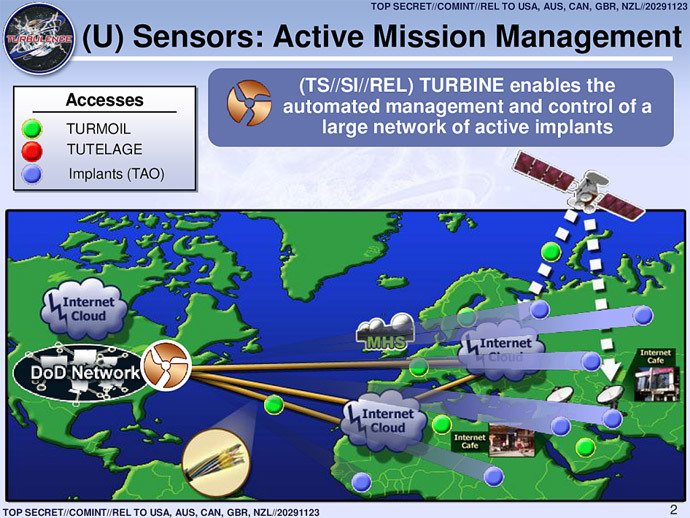
According to The Intercept, the NSA has escalated offensive cyber operations significantly since 2004 in order to spy on targets, and has used an array of tactics and “implants” that were previously undisclosed in order to carry out these missions.
The website reported that the agency’s British counterpart, the GCHQ, “appears to have played an integral role” with regards to developing these implants, which have grown in number exponentially in recent years from only 100 or so to tens-of-thousands, according to the report.
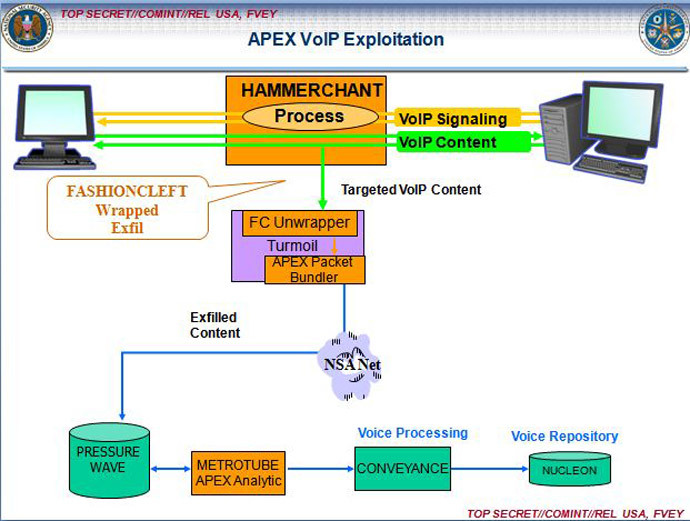
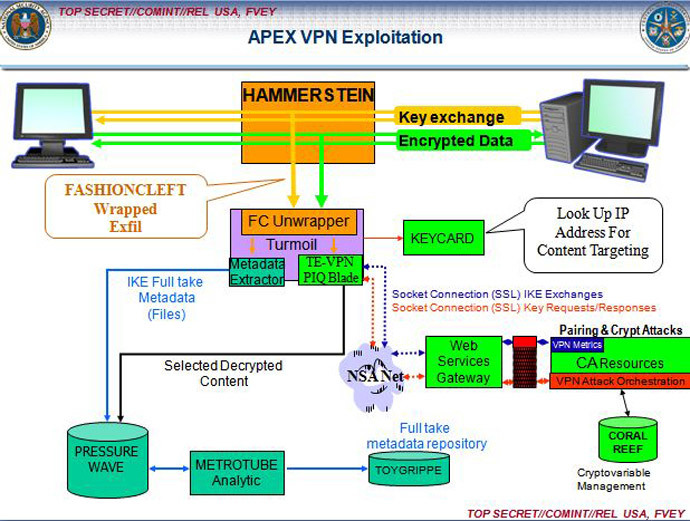
These implants, the journalists wrote, allow the NSA “to break into targeted computers and to siphon out data from foreign Internet and phone networks.” They can also be combined with a number of specialized plugins to provide analysts with additional surveillance options, the likes of which could likely leave many thinking staying secure on the Web seem impossible after reading the Greenwald and Gallagher report.
In one example cited by The Intercept, the NSA disguised itself as a fake Facebook server in order to intercept connections attempted to be made between account holders and the social networking site’s real computers. Instead, however, the NSA sends those unsuspecting Facebook users to a real site embedded with malware that then has the ability to infect that target’s computer.
That program — QUANTUMHAND — became operational in October 2010, The Intercept reported, after it successfully allowed the NSA to gain access to “about a dozen targets.”
A spokesperson for Facebook told The Intercept he had “no evidence of this alleged activity,” but QUANTUMHAND is far from the only program that, thanks to Edward Snowden, have linked the NSA to relying on already established websites and programs to pry into the communications of targets.
In another example, The Intercept included images from an internal NSA slideshow presentation that indicates surveillance missions can be waged by the agency against targeted email addresses, IP addresses and the “cookies” created by websites like Google, Yahoo, YouTube and countless others to track visitors, often for advertisement and user experience purposes.

Ashkan Soltani, a DC-based independent security researcher, remarked on Twitter that the information in that presentation “looks a lot like a catalog of ad tracking tech.” Instead of being used by the likes of Google to give YouTube users a more “personalized” browsing experience, however, the NSA and GCHQ can use these selectors to spy on the habits of unknowing subjects of investigation.
GCHQ targeting sheet looks a lot like a catalog of ad tracking tech: UDIDs, Google prefIDs, doubleclickID, WiFi MAC pic.twitter.com/oOMl0yJj4k
— ashkan soltani (@ashk4n) March 12, 2014
Other programs disclosed by Mr. Snowden and described by The Intercept include CAPTIVATEDAUDIENCE (“used to take over a targeted computer’s microphone and record conversations”, GUMFISH (“can covertly take over a computer’s webcam and snap photographs”), FOGGYBOTTOM (“records logs of Internet browsing histories and collects login details and passwords”), GROK (“used to log keystrokes”) and SALVAGERABBIT to exfiltrate data from removable flash drives connected to a target’s computer.
To infect computers with these implants, The Intercept said, the NSA can avoid trying to trick targets into going to fake websites by instead spamming them with unsolicited email containing links to malware.
“If we can get the target to visit us in some sort of web browser, we can probably own them,” an NSA employee wrote in one of the previously secret documents. “The only limitation is the ‘how.’”
The Intercept’s latest report was published only two days after Snowden spoke remotely to the audience of the SXSW Interactive tech conference in Austin, Texas and urged attendees to use encryption — a tactic, he said, that is still relatively successful with regards to thwarting snooping like the kind carried out by the NSA.
Encryption, Snowden said on Monday, makes it“very difficult for any sort of mass surveillance”to occur.
If The Intercept’s report is anywhere close to representative of the NSA’s actual capabilities though, then the agency’s operations are expanding regardless and relying on new tricks and techniques to track down and monitor persons of interest in the name of national security.
“When they deploy malware on systems,” malware expert Mikko Hypponen told The Intercept, “they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties.”














